Image Authentication Strategies from OSINT Certified Experts
By Carla Rodriguez | Mar. 5, 2025 | 6 min. read
What You Will Find Below:
- What is Image Authentication
- The Uses of Image Authentication
- Deep Fakes
- Shallow Fakes
Image Authentication is an essential process for verifying the integrity of images and videos, ensuring they haven’t been altered or manipulated. As technology advances, so does the ease of manipulating digital content, making it critical to confirm the authenticity of visual evidence, especially in industries like insurance and law.
Understanding how Image Authentication works, its real-world applications, and the tools available can help you make smarter, more confident decisions.
What is Image Authentication?
Image Authentication is the process of verifying the integrity of an image or video to ensure that it has not been altered, manipulated, or misrepresented.
Every image goes through a three-step process from capture to verification:
The Point of Capture
When a camera captures a photo or video, it automatically leaves a unique fingerprint at the source. This ‘virtual fingerprint’ encompasses the contents of the image, as well as sensitive metadata.
Metadata refers to the detailed information embedded in an image. This includes specific details like the time, location, and “author” of the image.
Photographic metadata, known as EXIF (Exchangeable Image File Format), includes details such as the camera model, exposure, and aperture, and can also reveal when and where the photo was taken. This data can be used to verify whether the image was created on a specific device or if it’s a screenshot or reused image.
Actionable Tools:
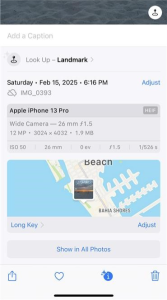
Here’s a quick example of metadata you can access right now: If you’re using an iPhone, open the image you want to analyze and swipe up. A tab will appear with detailed information about the image, including details like location, date, and camera settings.
On Android, tap the image and go to Properties > Details. Here, you can find the metadata, including details such as which lens was used to capture the image and whether the flash was activated.
Could your claimant’s image be a duplicate? A reverse image search can help you find out:
Reverse image search tools like Google are incredibly valuable for claims verification, providing an easy way to detect potential fraud. By uploading the claimant’s image to Google, you can quickly check if the same image appears elsewhere online. If it does, it’s likely not their original photo, indicating that the image may have been reused or manipulated—pointing to a potentially fraudulent claim. This simple tool can be a game-changer in identifying dishonest attempts and ensuring the integrity of the claims process.
Differentiating the Fingerprints
Image tampering typically leaves behind ‘virtual fingerprints’—distortions or irregularities within the image. However, since each image is unique and tampering methods vary based on the fraudster’s intent, these fingerprints can differ significantly from one case to another. Some of the most helpful fingerprint features are resampling, multiple compressions, duplicated regions, and noise inconsistencies.
Resampling:
Resampling is the process of altering the dimensions of an image, making it either smaller or larger. When someone tampers with an image, they may resize or resample it to fit a different context or conceal evidence. This adjustment changes the pixel values, impacting the image’s resolution or size, and often leaves behind detectable traces of manipulation.
Multiple Compressions:
Each time an image is compressed, it loses some quality and important details that could serve as evidence. For example, imagine you have a photo on your computer. First, you compress it into a JPEG format, and then compress the already compressed image again into a PNG. Now, the image has undergone multiple compressions. To verify its authenticity, you would reverse the compression process. If the different stages don’t align, it’s a clear indication that the image has been tampered with.
Duplicate Regions:
Duplicate regions occur when a section of an image is copied and placed in multiple areas to hide or alter part of the picture. While this can be hard to spot for the untrained eye, it becomes easier with experience. For example, someone might copy a section of a damaged fence and cover up an area that wasn’t damaged, making it look like the damage occurred in a way that matches their fraudulent claim.
Noise Inconsistencies:
Noise inconsistencies occur when irregularities or variations appear in the background of an image, which can be used to question its authenticity. In an unaltered photo, the level of blur or noise should remain consistent across the image. However, if the image has been tampered with, certain areas may show an uneven or increased blur. For example, in a fraudulent claim where someone alleges their diamond ring was stolen, you might notice an inconsistent blur around their hands, indicating that part of the image has been altered.
The Uses of Image Authentication
In a court of law, images are now treated with the same level of scrutiny as written documents. In People v. Beckley, the court ruled:
‘A photograph is a “writing,” and “authentication of a writing is required before it may be received into evidence.”’
This highlights the importance of image authentication, particularly when the image serves as key evidence or when there’s a risk that the case could escalate to litigation.
Any of the following instances require image authentication:
1. Presenting footage in court
2. Verifying/denying a claim
3. Investigating case evidence
Advancements in photo editing software have made it easier for people to manipulate images to avoid a claim or secure a settlement payout. Today, we’re seeing tampered images ranging from fake injuries to altered accident scenes.
(The Guardian, 2024)
Shallow Fakes
Shallow fakes are manipulated media that require minimal effort to alter, often involving simple edits like cropping, resizing, or color adjustments. These low-effort fakes are becoming increasingly common and pose a growing threat to the insurance industry, as they can easily deceive untrained eyes. Without proper authentication systems in place, many insurers unknowingly approve fraudulent claims based on these shallow fakes, resulting in unnecessary payouts.
For example, someone might alter an image to falsely depict an injury or accident. This type of manipulation can drive up premiums for everyone, including those who aren’t involved in the fraud. The real cost to insurers is the financial loss from paying out claims based on these fabricated scenarios.
Deep Fakes
Deep fakes take things to a whole new level, using advanced AI and machine learning to create hyper-realistic videos and images. These fakes can swap faces, manipulate voiceovers, or even generate completely fabricated scenarios, making them much more difficult to detect than shallow fakes.
In the insurance world, deep fakes can have even more severe consequences. Fraudsters can craft entirely fake accidents or injuries, mimicking real people and events with striking accuracy.
Without proper detection tools, insurers risk approving fraudulent claims, leading to significant financial losses and higher premiums for all policyholders.
What Can You Do?
Staying up to date on technology and image authentication practices is a powerful way to stay one step ahead of fraud. By recognizing potential red flags, you will be empowered to identify inconsistencies to ensure that nothing slips through the cracks. For even more accurate results, consider bringing in experienced video forensics experts to analyze everything from file conversions to metadata.
Click here to explore our full library of blog topics, including OSINT, GenAI, Internet Mining, and all other digital investigation resources.
Want to elevate your fraud detection strategy? Contact our digital investigations department today and address your specific questions and challenges.
